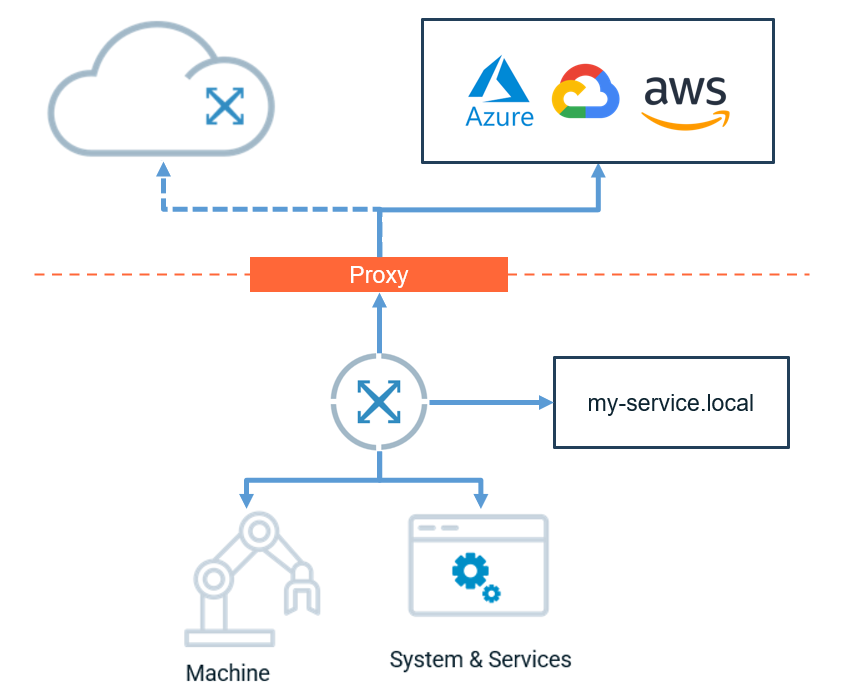
Crosser Node behind proxy
This article shows how to run the Crosser Node behind an HTTP/HTTPS proxy while still reaching local/on-prem systems without the proxy.
-
The Crosser Node is a .NET application.
-
On Windows, it reads the http_proxy, https_proxy, and no_proxy system environment variables.
-
On Linux/Docker, it follows the standard http_proxy, https_proxy and no_proxy.
-
If your proxy performs TLS inspection (MITM) or serves via a private CA, the Node must trust the proxy’s root/intermediate certificates.
Docker
Set proxy variables on the container and use NO_PROXY to list hosts that must bypass the proxy (local databases, brokers, internal APIs, etc.).
To trust a corporate proxy CA, either:
-
mount a trusted CA bundle from the host into the container, or
- bake the CA into a custom image
services:
edgeNode:
image: registry.crosser.cloud/node/edgenode:latest
container_name: crosser-edgeNode
restart: always
environment:
# --- Crosser credentials (required) ---
- SecurityConfiguration__Credentials__NodeId=ENTER-YOUR-NODEID-HERE
- SecurityConfiguration__Credentials__AccessKey=ENTER-YOUR-ACCESS-KEY-HERE
# --- Proxy settings (OPTIONAL) ---
# Use http://user:pass@proxy.example.com:3128 if authentication is required.
- HTTP_PROXY=http://proxy.example.com:3128
- HTTPS_PROXY=http://proxy.example.com:3128
# Duplicate in lowercase for tools/libraries that only read one variant.
- http_proxy=http://proxy.example.com:3128
- https_proxy=http://proxy.example.com:3128
# Hosts that should BYPASS the proxy (comma-separated):
# include localhost, container service names, Docker host alias, and intranet domains.
- NO_PROXY=localhost,127.0.0.1,::1,host.docker.internal,edgeNode,*.local,db,influxdb,mosquitto,my-internal-api.corp.local
- no_proxy=localhost,127.0.0.1,::1,host.docker.internal,edgeNode,*.local,db,influxdb,mosquitto,my-internal-api.corp.local
ports:
- 9090:9090
- 9191:9191
- 1883:1883
volumes:
- "./data:/application/data"
# Map the Ubuntu host's trusted CA bundle into the container (READ-ONLY).
# Ensure your corporate/proxy root CA is installed on the host (see notes below).
- "/etc/ssl/certs/ca-certificates.crt:/etc/ssl/certs/ca-certificates.crt:ro"
# Alternative: map the whole directory if preferred (comment the single-file line above)
# - "/etc/ssl/certs:/etc/ssl/certs:ro"
# Alpine-based images often use /etc/ssl/cert.pem. If needed, add:
# - "/etc/ssl/certs/ca-certificates.crt:/etc/ssl/cert.pem:ro"
logging:
driver: json-file
options:
max-size: "50m"
max-file: "2"
Notes
-
Add your proxy CA to Ubuntu (host): place proxy-root.crt in /usr/local/share/ca-certificates/ and run sudo update-ca-certificates. This updates /etc/ssl/certs/ca-certificates.crt, which the container mounts.
-
Local services in Compose: Add each service name you connect to (e.g., db, mosquitto, influxdb) to NO_PROXY.
-
Docker host from Linux containers: if you call services on the Docker host, include host.docker.internal (on Linux you may need to add extra_hosts: - "host.docker.internal:host-gateway" and Docker 20.10+).
Windows
The Crosser Node (being .NET) reads Windows system environment variables: http_proxy, https_proxy, and no_proxy. Use no_proxy to bypass the proxy for local/intranet hosts. On Windows, you have different ways to set the proxy configuration.
Option 1. Set system environment variables (GUI)
-
Open System Properties → Advanced → Environment Variables…
-
Under System variables, add or edit:
-
http_proxy → http://proxy.example.com:3128
-
https_proxy → http://proxy.example.com:3128
-
no_proxy → localhost,127.0.0.1,*.local,host.docker.internal,db,influxdb,mosquitto,my-internal-api.corp.local
-
-
Restart the Crosser Node service (or reboot) so it picks up the changes.
Option 2. Set via PowerShell (as Administrator)
Powershell:
[System.Environment]::SetEnvironmentVariable('http_proxy', 'http://proxy.example.com:3128', 'Machine')
[System.Environment]::SetEnvironmentVariable('https_proxy', 'http://proxy.example.com:3128', 'Machine')
[System.Environment]::SetEnvironmentVariable('no_proxy', 'localhost,127.0.0.1,*.local,host.docker.internal,db,influxdb,mosquitto,my-internal-api.corp.local', 'Machine')
# Restart the Crosser Node Windows service afterwards.
Option 3. Set in Node's configuration file
You might find yourself in a situation where your users gets the proxy configuration when login to Windows (group policy, login-script, ...) but the Node is not aware of that proxy, since it is executed as a service. In this case, set the proxy settings in the local configuraiton file ./data/endpoints.json.
"httpProxy": {
"host": "http://proxy.example.com:3128",
"user": "",
"password": ""
},
"httpsProxy": {
"certificate": "",
"useTls": false,
"host": "http://proxy.example.com:3128",
"user": "",
"password": ""
}
Once that is done, restart the Node service.
2. Trust the proxy certificate
If your proxy uses a private/root CA, import it so the Node trusts outbound TLS through the proxy.
-
GUI (MMC):
-
mmc.exe → File → Add/Remove Snap-in… → Certificates → Computer account → Local computer.
-
Under Trusted Root Certification Authorities → Certificates, Import… your proxy root CA (.cer/.crt).
-
(If applicable) import intermediates under Intermediate Certification Authorities.
-
Powershell:
Import-Certificate -FilePath "C:\certs\proxy-root.cer" -CertStoreLocation "Cert:\LocalMachine\Root"
Notes:
- Make sure the variables are set at the Machine scope if the Node runs as a Windows Service (e.g., LocalSystem). Then restart the service.
Search Documentation
Page Sections
